Lessons Learned from 100+ Cases of Ransomware
08/06/2023

By Imelda Flores – Head of SCILabs, Scitum
The countries of Latin America and the Caribbean are the perfect sandbox for ransomware attackers, Imelda Flores noted during her presentation at LACNIC 39. The reason for this is the large number of legacy and older devices and equipment in the region. Hackers know that in the event of an attack the response will not be strong, which makes LAC an ideal stage for attacks. According to Flores, the fragility of the region in this regard has allowed it to become the target of attack techniques that are being tested for the first time, seeking to increase the harm caused by ransomware attacks.
Imelda Flores heads the SCILabs team at Scitum-Telmex, where their tasks include responding to security incidents worldwide, automating complex security operations, cyber intelligence, and coordinating investigations into advanced malware and campaigns affecting the region.
During the LACNIC Technical Forum, the expert spoke about the more than 100 ransomware incidents in Latin America to which the SCILabs team has responded.
CROWN JEWEL. Flores warned that ransomware attackers love to use valid accounts to gain access to an organization, and they typically use these on remote web-exposed desktops, VPNs without multi-factor authentication (MFA), or Citrix servers that are not behind a firewall, but they can also take advantage of vulnerable devices connected to the Internet. Once inside an organization, attackers seek to escalate their privileges and reach the Active Directory. “Today, the Active Directory is an organization’s crown jewel,” said Flores. Attackers have found that it is the nerve center of any organization, and that when the Active Directory becomes unavailable, virtually every operation fails.“From there, they can move on to storage, to the organization’s database, to any other Active Directory, or wherever they want,” she explained.
Once they reach a database or another location from where they can extract information, they encrypt the organization’s critical equipment. Faced with this situation, many organizations are willing to pay, not to recover the encryption key, but so that the stolen information will not be made public.
SIMULTANEOUS THREATS. “We’ve determined that attackers wait between one and two weeks after they breach a system before deploying a ransomware attack,” Flores explained. “An attacker may be interested in installing ransomware within an organization, but at the same time other threats may exist. On occasion, we’ve seen two or three types of attackers at the same location, on the same server, at the same time, but with different goals,” she added.
When deploying ransomware, attackers simultaneously try to perform a cleanup. Why? To complicate the work of the people investigating this type of attack. Finding the artifact that performed the encryption is essential to understand how the attack occurred, the origin from which the ransomware was distributed, and which other devices were compromised.
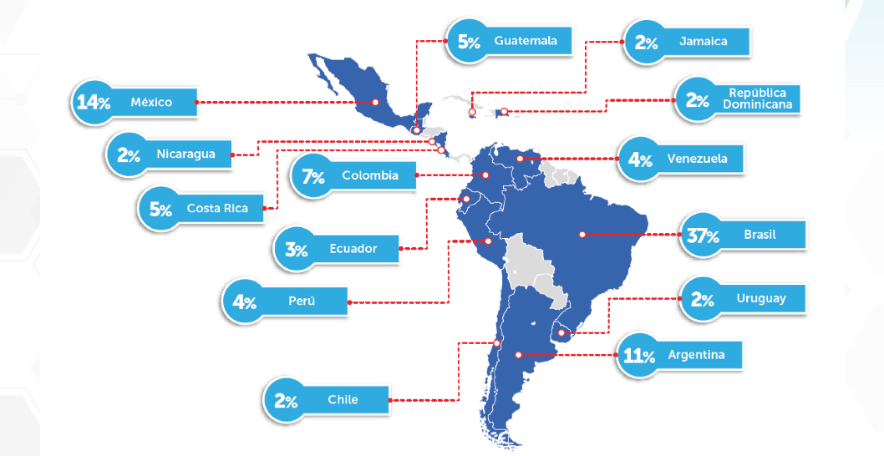
AFFECTED COUNTRIES. According to the report published by Scitum-Telmex’s SCILabs, Brazil, Mexico and Argentina topped the ranking of ransomware attacks during the second half of 2022.
As for the type of ransomware used by attackers in the region, the study detected several very active groups or families: Lockbit 3.0 (50% of attacks), Blackbit (7%), and Blackcat (7%).
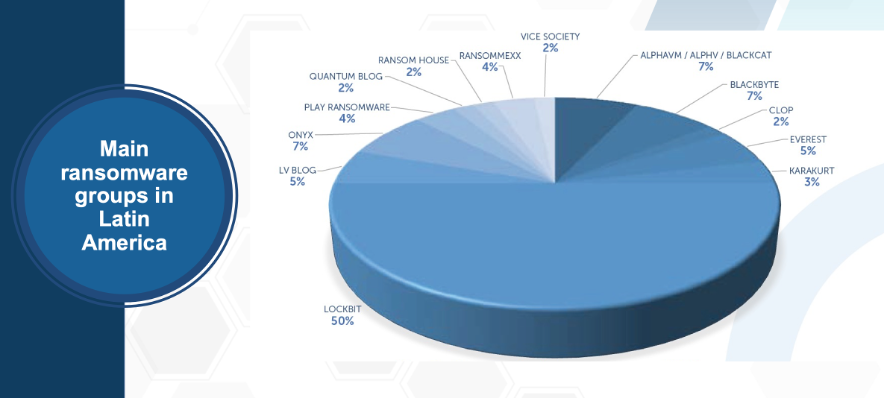
Flores admitted that several ransomware groups are fighting over the LACNIC service region. According to Flores, the model works as follows: affiliates pay to launch ransomware attacks developed by others, sometimes two or more ransomware at the same time. “Typically —she added— 25% of the ransom paid goes to the developer, while 75% goes to the party who executes the attack.”
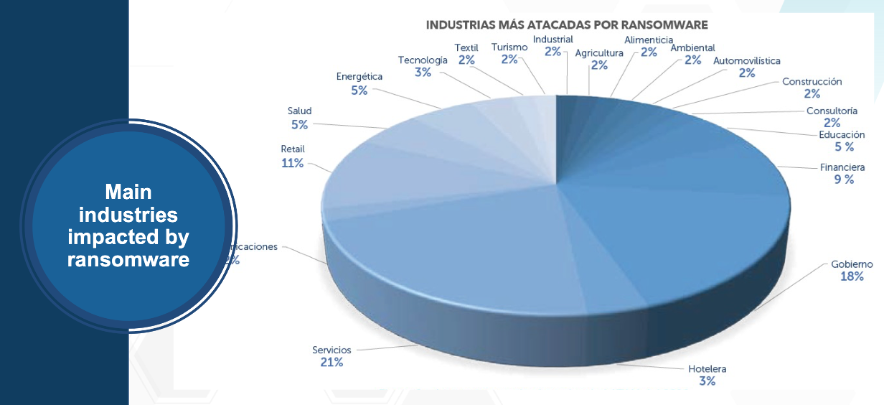
NOT MERELY FOR FUN. The Scitum-TELMEX SCILabs team has determined that the service industry, governments, the financial sector, the hospitality industry, and several manufacturing industries are the organizations of choice for ransomware attackers (see image below). Ransomware attackers choose their targets based on how much pain they can cause, in other words, where the damage will be enough for the organization to pay the ransom. “Attacks are not merely for fun,” Flores said.
LESSONS LEARNED. Flores detailed a series of lessons learned in the race against the attackers.
- First, she pointed out that the initial reaction to the event should not be treated as a sprint. “This is a marathon. The investigation alone takes four to six weeks. Recovery will take several days, weeks, or even months. This is why our recommendation is to let part of the staff rest, as the recovery process will be long. Answering the question of how an attack took place will take more than two days,” the expert noted.
- Second, she observed that organizations do not prioritize investigating where an attack originated.Dealing with ransomware involves several parts. One has to do with the investigation, a race to find the malicious artifacts that will provide an idea of the attacker’s actions. Another part is recovery, which can take anywhere from days to months.
- A third important part is communication. Flores pointed out that in Latin America, organizations that have fallen victim to an attack often act as if nothing had happened. However, she stressed the need to adopt the opposite approach, as transparency both within and outside the organization is very important. “One of our customers specifically asked us for a document explaining the attack vector they had experienced, the indicators of compromise, and recommendations. They approached their most important customers and explained that they had been compromised and showed them how this had happened. This organization increased their business because of the trust they generated,” she exemplified.
There are always information leaks, even if there is no evidence of exfiltration. All ransomware cases studied by the SCILabs team show that attackers extract information. “Even if there is no evidence, exfiltration has likely occurred.” The most destructive attacks happen on weekends and holidays, precisely when organizations tend to let their guard down. Flores stressed that preparation is key and that minimizing the risk is very feasible. “This does not mean that it won’t happen, but practicing what to do during a ransomware attack can help us be better prepared for a situation like this,” she concluded.