Validating MANRS with FORT Monitor
26/03/2024

By Erika Vega, Senior Consultant at SOCIUM and Engineering Manager at MC&H Networks
When an organization connects to the Internet and starts sending and receiving data packets using its own Internet number resources such as Autonomous System numbers and IPv4 or IPv6 addresses, it becomes an identifiable entity within this network of networks. This comes with both risks and responsibilities. These risks include the possibility of malicious parties obtaining data on how information is transmitted and published to and from your network, while the responsibilities involve understanding what actions we can take to protect our organization and other entities with whom we exchange data.
There are multiple actions that a network operator with its own resources can implement to strengthen and improve their routing infrastructure security. These actions range from training and awareness initiatives to the implementation of filtering and applying best practices in the logical configuration of routers.
MANRS Compliance in the LAC Region
Better known as MANRS, the Mutually Agreed Standards for Routing Security represent a global initiative that provides a framework of specific actions and critical solutions for reducing the most common threats to routing security. These actions are grouped in four programs: Network Operators, Internet Exchange Points, CDN and Cloud Providers, and Equipment Vendors.
Included below is an example of the actions specified for Network Operators, along with their compliance based on measurements conducted in the LAC region during the month of March.
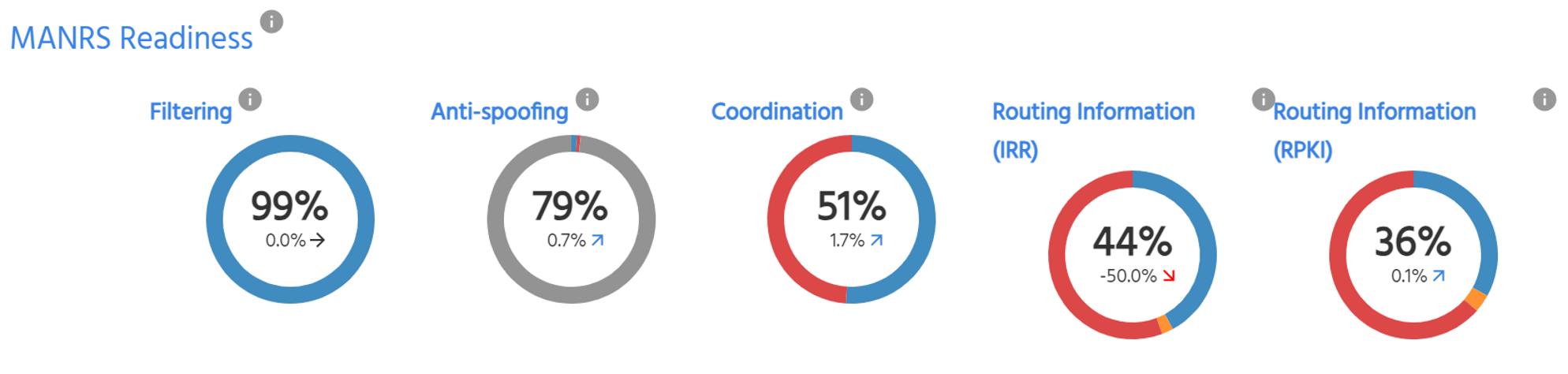
As the image shows, adoption and utilization of mechanisms such as Resource Public Key Infrastructure (RPKI) and distributed Internet routing registry databases (IRR) remains below 50%, despite the fact that they are integral for complying with the MANRS global validation action. Therefore, it is crucial to work to increase their deployment in the region, leveraging tools that allow us to validate the status of our announcements in terms of compliance with these measures.
FORT Monitor
Many tools have now been developed to help organizations visualize how announcements are advertised through the global routing system. These tools provide valuable information to facilitate decision-making and the implementation of actions to improve security in our own routing scheme and, consequently, in overall routing.
(Free access, no subscription required)
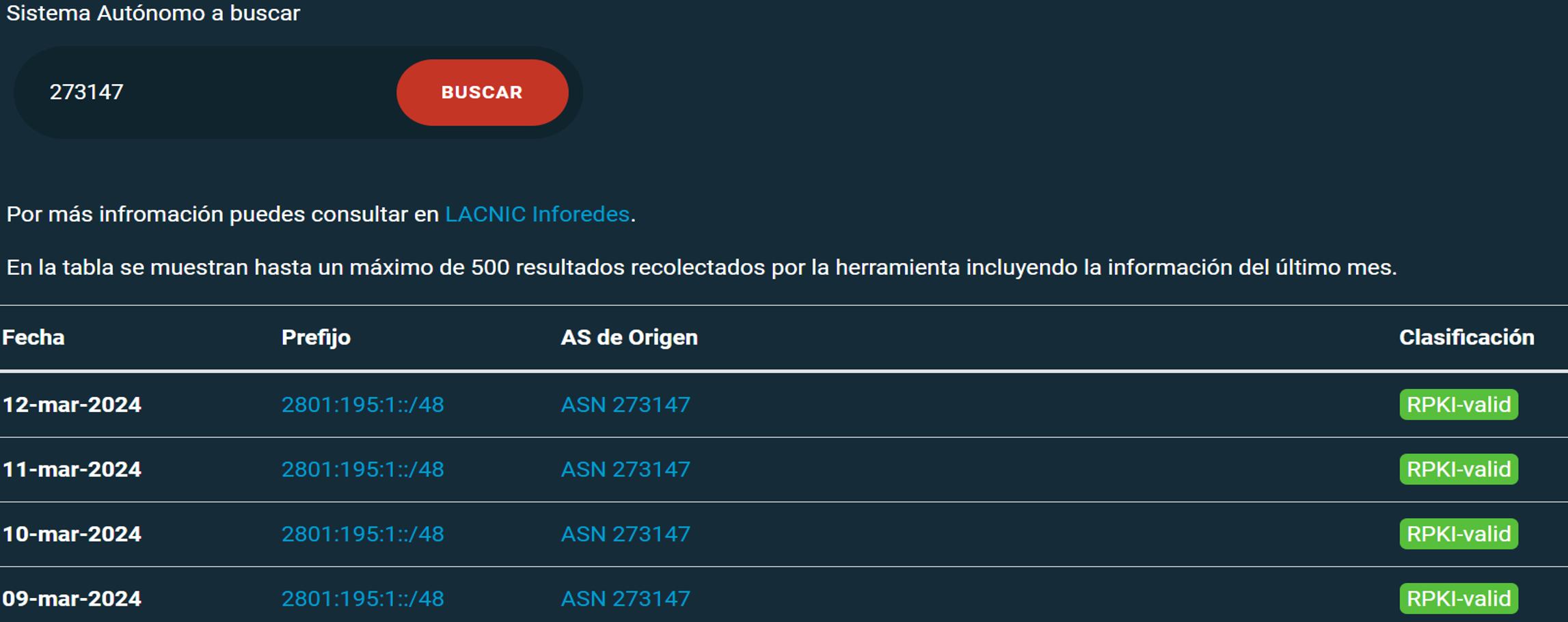
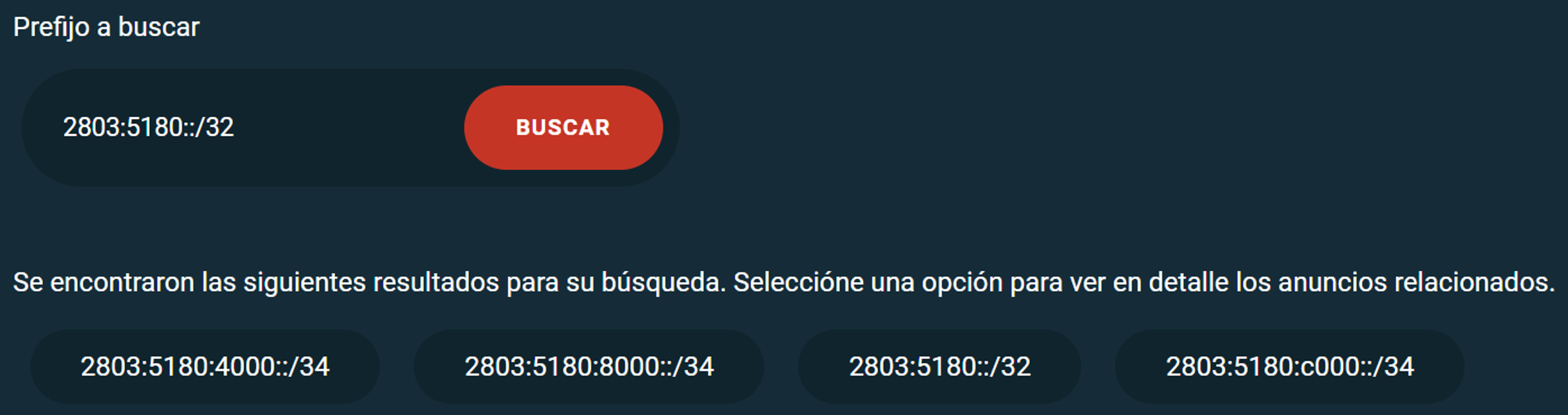
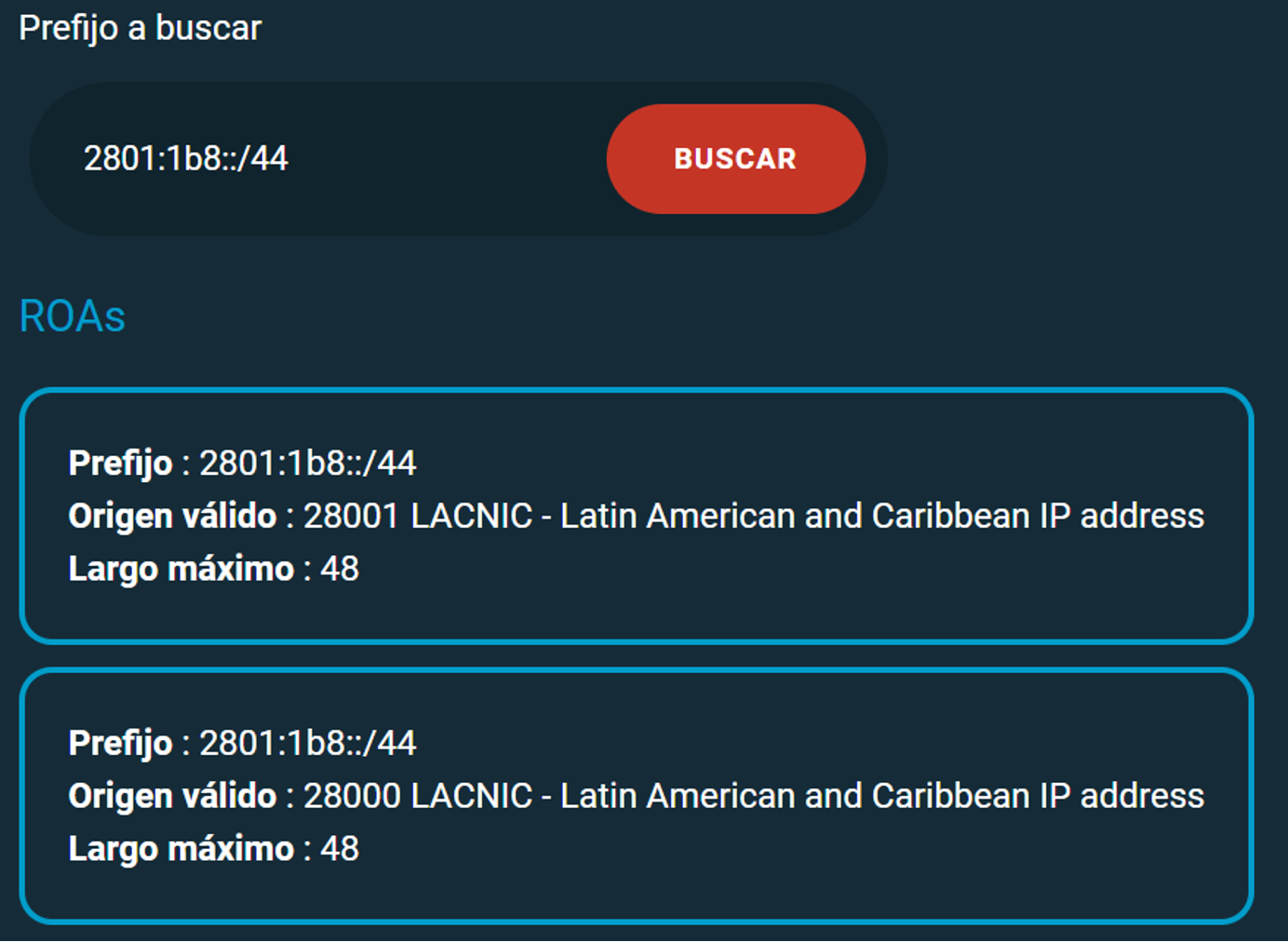
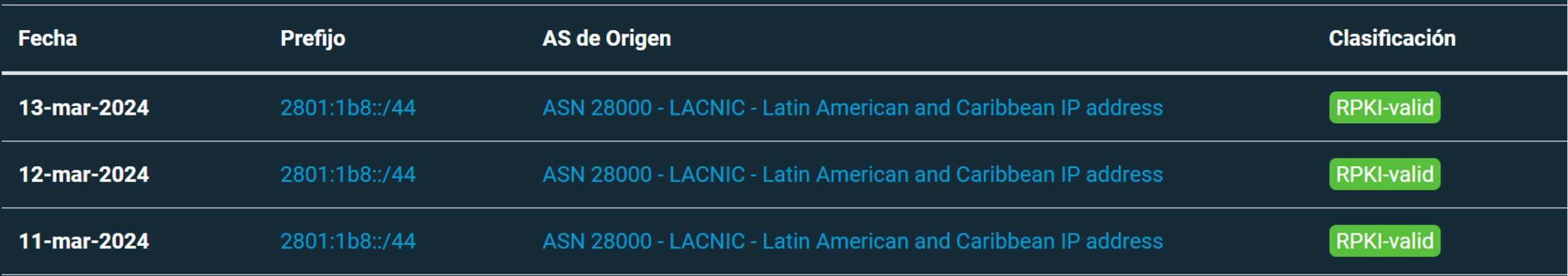
One such tool is FORT Monitor, the result of a initiative by LACNIC. This freely accessible tool allows us to examine in detail an organization’s announcements and their validity status, either by prefix or by Autonomous System. It also provides simplified data on the status of routing security in the LAC region.
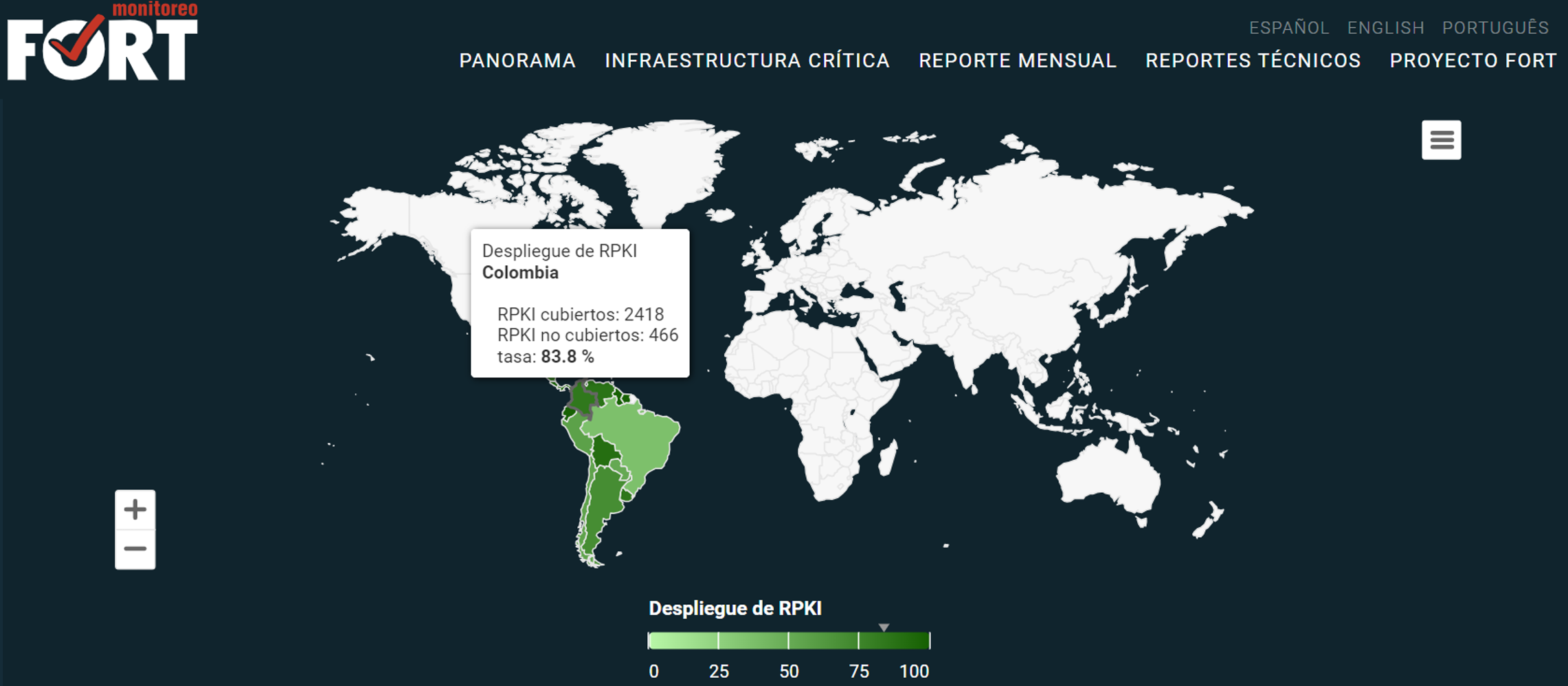
Where Does Fort Monitor Obtain Its Data?
FORT Monitor collects BGP announcement data using the UPDATE messages of the collectors available in CAIDA’s open source BGPStream software. It then classifies the data based on their validity statuses, identifying them thanks to the queries to the FORT and Routinator RPKI validators.
To validate the IRR’s routing records, FORT uses the data available in the RADB and RIPE databases. Finally, in order to produce reports at the regional level, it correlates the prefixes in these BGP announcements with the countries within the LACNIC service region, using the information contained in the delegated-extended file for the blocks managed by LACNIC.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.