Security Threats and Controls for Mitigating DoS/DDoS Attacks
23/07/2024

By Graciela Martínez and Guillermo Cicilieo
DoS/DDoS (Denial of Service/Distributed Denial of Service) attacks are one of the most common concerns for ISPs. Due to their role in digital infrastructure, ISPs are attractive targets for cybercriminals who can attempt to compromise their network, disrupting their different services.
In this context, we conducted interviews with professionals from various organizations in Latin America and the Caribbean. Our goal was to understand their perspective and based on their experience, have an initial overview of the security threats they face and the extent to which they have implemented controls for their mitigation.
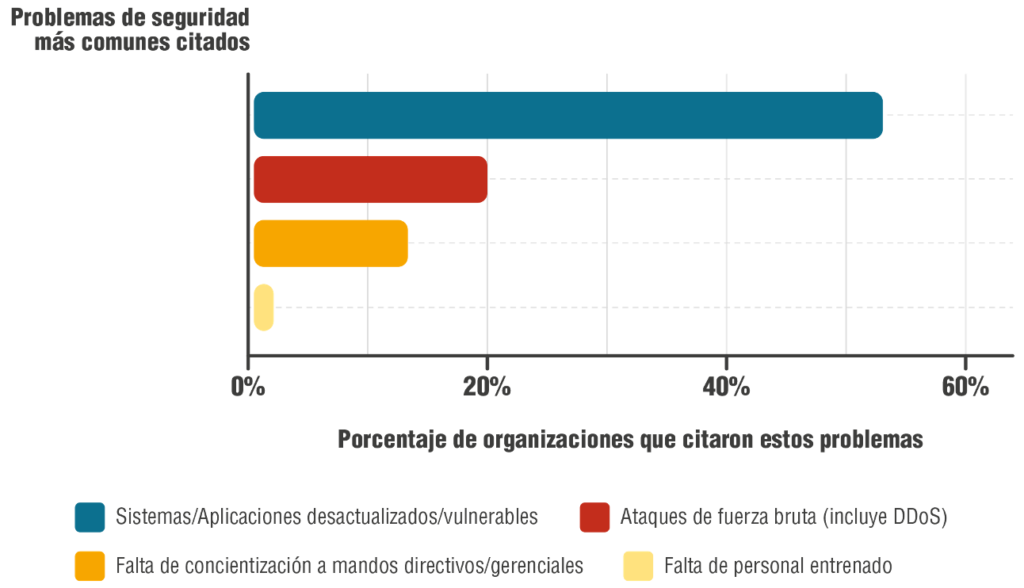
During this findings identification phase, we detected key aspects of the most common issues faced by ISPs.
More actions are necessary
According to the interviewees, all organizations recognize the importance of cybersecurity for protecting assets and ensuring business continuity, yet many acknowledge the need to continue working on implementing more actions. Indeed, there is an awareness that cybersecurity must be included in an organization’s roadmap as part of its strategy. However, it is often not considered a strategic objective and, instead, security activities are scattered across daily operations.
To deal with the challenges that are emerging in the digital landscape in organizations such as ISPs, it is essential to proactively protect the infrastructures that support the business and promote a safe and reliable online environment for all.
According to information provided by the experts we consulted, the main reasons for this management issue can be divided into the following aspects:
- Overdue updates. The lack of hardware, software, and firmware is a common threat. Failure to manage updates and patches represents a risk for organizations, as outdated systems are one of the main attack vectors exploited by cybercriminals.
- Lack of preparation among organizations’ security personnel and lack of awareness at the management level.
- Organizations’ internal lack of knowledge about threat detection. Only a third of the professionals surveyed, all of whom serve in administrative roles within their organizations, admitted to having a security incident reported in the last three months. This result might seem encouraging, but it shows significant under-reporting: the fact that a security incident has not been detected or reported does not mean that it has not occurred.
Most popular tools
The following graph shows the most well-known tools mentioned in the interviews. However, some organizations have not implemented these solutions due to their high cost.
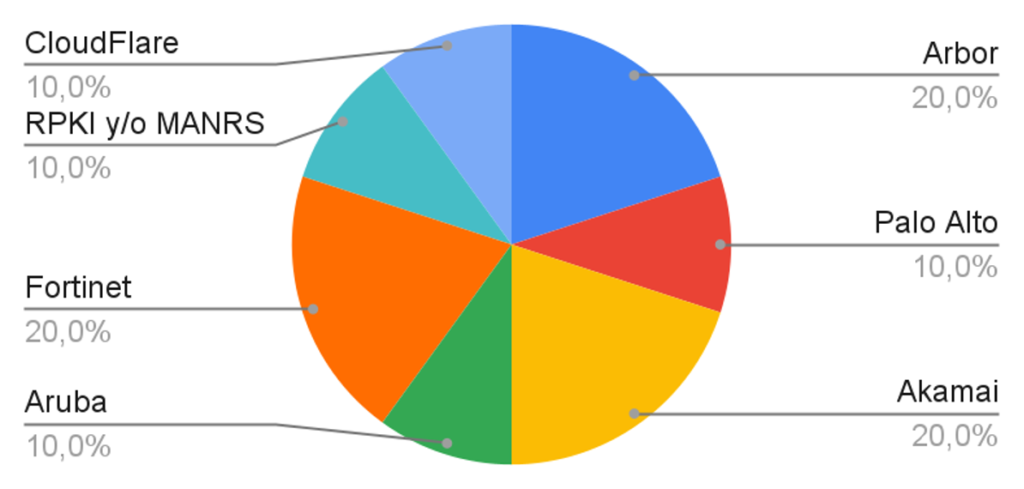
It should be noted that, despite not being anti-DDoS attack tools, many interviewees mentioned RPKI (Public Key Infrastructure) and MANRS (Mutually Agreed Norms for Routing Security) as useful tools to prevent DDoS attacks.
LACNIC support
LACNIC works on strengthening cybersecurity as a strategic issue for ISPs and promotes the training of senior management on the importance of managing this issue within each organization.
We found that professionals from the organizations we interviewed aren’t in the habit of sharing their best practices with their peers, and often work in isolation in the implementation of control mechanisms and incident containment. At LACNIC, we aim to create opportunities and spaces for exchanging best practices and recommendations on cybersecurity so that everyone can be prepared.
At LACNIC CSIRT, we encourage our members’ participation in projects such as HoneyNet, which aim to strengthen security monitoring capabilities and improve early detection of attacks in the region.
We invite you to check out the information and resources LACNIC provides to address this community’s issues and interests, including R&D technical reports and articles on cybersecurity available on our blog.