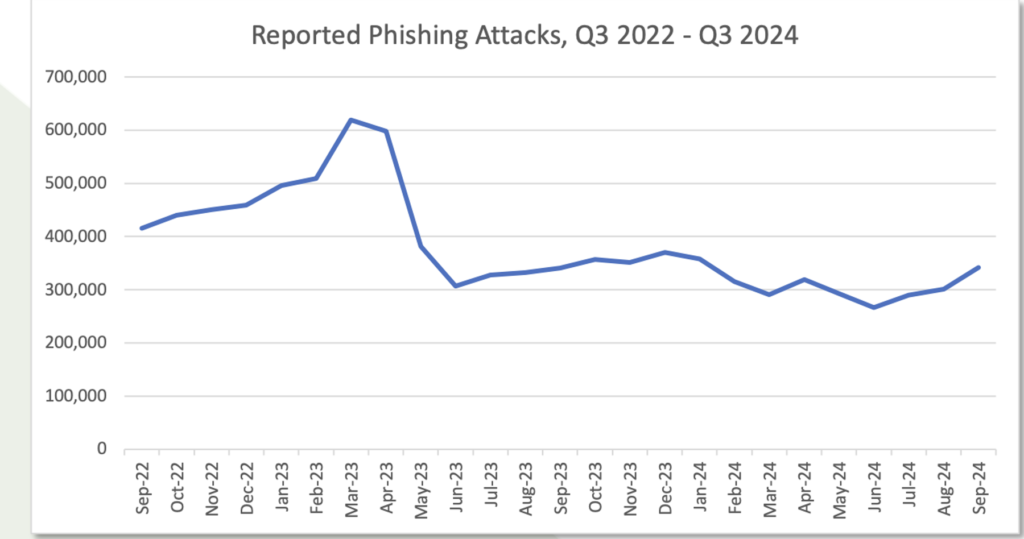
Phishing continues to evolve with new tactics designed to deceive users and compromise their information. This year, we want to highlight three trends that stand out in the cyberattack landscape: the rise of smishing, the increasing use of cloud hosting for phishing, and the use of artificial intelligence as a tool for more sophisticated attacks.
Smishing, a form of phishing that uses text messages (SMS) to deceive users, accounted for 39% of mobile phone threats in 2024. According to Proofpoint, it has increased by more than 300% since 2023.
Cybercriminals impersonate banks, messaging companies, government entities, and others to trick victims into clicking on malicious links, sharing personal information, or downloading malware to their devices.
Smishing attacks are a form of social engineering that uses various techniques to manipulate people into revealing sensitive information or taking action without prior thought.
How Does Smishing Work?
Attackers send text messages that appear to come from legitimate sources, such as a bank, a messaging company, or a government entity.
Smishing messages typically include a malicious link to a fake website, a fraudulent phone number to deceive the intended victim, and an urgent message designed to create fear or pressure, such as “Your account will be blocked if you don’t update your data now.”
Smishing Success Factors
Scale: There are more than 6 billion mobile phone subscribers in the world. According to the World Bank, the number of mobile subscriptions exceeds the global population, possibly because many individuals use multiple mobile lines.
Click rate: SMS messages have an average click rate of approximately 20%, compared to 3-5% for email messages.
Trust in SMS messages: People tend to trust text messages more than emails, as SMS is often associated with personal communications. Additionally, people trust their operators.
Immediacy and urgency: Smishing messages create a sense of urgency in order to lead victims to act quickly without taking time to analyze the situation.
Personalization and credibility: Smishing messages may contain personal information about the victim and this increases their credibility.
Recommendations to Avoid Falling Victim to Smishing
- Don’t trust unexpected messages, especially from unknown phone numbers.
- Avoid clicking on links you receive via SMS, as they may redirect you to malicious websites.
- Verify the sender’s identity. If you receive a text message from a company or entity, verify its authenticity by reaching out to them directly through their official phone number, email address, or website.
- Never share personal or financial information via text message or any other unverified method. No legitimate organization will request confidential information through SMS or any informal channel.
- Report smishing messages to the CSIRT of company or entity that is being impersonated.
2. Cloud Hosting Phishing
Cybercriminals are increasingly hosting their phishing sites on cloud hosting networks, which allows them to expand quickly and avoid being blocked. By 2024, 77% of phishing sites will be hosted on cloud infrastructure, according to Netcraft.
A study conducted by Interisle confirms that, for the third consecutive year, Cloudflare remains the most widely used network for hosting phishing sites.
Cybercriminals register domain names that are very similar to those of legitimate organizations, and these are then used in mass phishing campaigns. This practice is highly effective due to its massive reach and the difficulties it presents for detection by security systems.
3. AI Phishing: Personalized and Precise
AI-driven phishing attacks are on the rise and increasingly difficult to detect because attackers use AI to generate realistic messages, both written and spoken, that appear to have been generated by humans. According to Zscaler ThreatLabs, these attacks have increased significantly, making it harder for traditional security systems to block them.
A report by Comcast Business reveals that 80% to 95% of cyberattacks begin with a phishing attack. In addition, since the launch of ChatGPT in 2022, the total volume of phishing attacks has increased by 4%, according to SlashNext.
According to FBI IC3 projections, AI-driven phishing attacks, such as whaling deepfakes, are expected to double in frequency by 2024-2025. This highlights the growing sophistication and use of AI tools in cybercrime.
Recommendations
To reduce the risk of phishing, it is critical for organizations to implement robust security measures and foster a culture of online security.
At LACNIC CSIRT, we promote training in security by educating employees, officials, and our constituency on how to recognize phishing and smishing attempts, as well as by highlighting the importance of reporting security events so that security incident response teams can manage them immediately.
Here are some recommendations.
From an organization’s perspective
- Train your employees. Teach them to identify and report phishing attempts, including through activities such as drills.
- Implement Multi-Factor Authentication (MFA) to access infrastructure, systems, corporate data, and personal information.
- Keep your systems up to date. Apply security updates immediately after their release; if that’s not possible, implement mitigation measures.
- Proactively monitor systems to detect suspicious activity.
- Have a CSIRT and an incident management plan.
From a user’s perspective
- Use strong passwords and enable two-factor authentication whenever possible.
- Don’t reuse your access credentials on different platforms.
- Back up your information stored on websites and make sure they are not connected to each other.
- Don’t click on links from unknown sites or download attachments from unfamiliar email addresses.
- Don’t download pirated software.
- Keep your systems up-to-date and only install updates from official sources.
Phishing continues to evolve, so it is crucial for both users and organizations to stay vigilant and adopt proper protective measures.