Most Common Infostealers in Our Region
04/09/2024

By Guillermo Pereyra, Security Analyst at LACNIC
As a follow-up to the article Infostealers: Prevention and Protection against Information Theft, in this article we present a more detailed analysis of the three most common infostealers in our region.
As the image shows, in our region, the three most common infostealers are RedLine, Raccoon, and Lumma. While the three share the common goal of stealing credentials and sensitive information, they differ in their infection methods, the types of data they target, and their evasion capabilities. Below, we will analyze each of them in detail.
RedLine
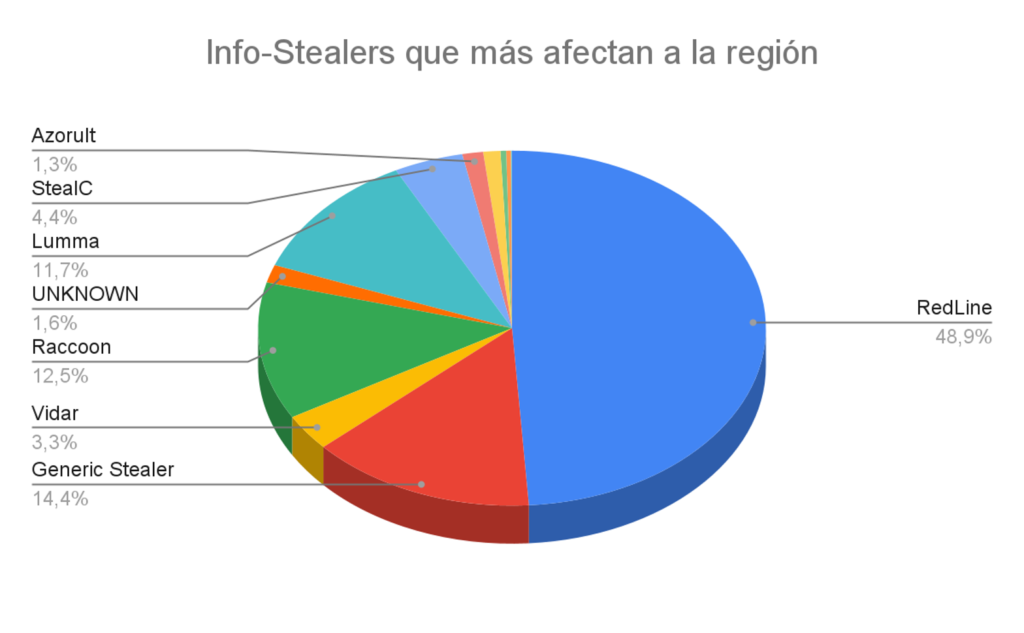
The image above shows that RedLine (blue) is common in this region. Source: Mcafee.
This is a type of infostealer malware that can be purchased on underground forums. Once obtained, criminals distribute the malware to their victims through scam websites that impersonate legitimate software, such as VPN clients or online file converters. Recent versions have also been detected in counterfeit games.
When a user runs the malware on their computer, it immediately begins its malicious activity. First, RedLine performs an anti-forensics analysis of the infected system to avoid detection and analysis. It then communicates with the command-and-control (C2) server, which instructs the malware what actions to perform on the victim machine.
Next, the malware proceeds to extract sensitive user data, including:
- Information about the victim system.
- Credentials, cookies, credit card details, and social media links stored in the victim’s browsers.
- FTP client data (FileZilla, WinSCP).
- Instant messaging client data.
- Cryptocurrency wallets; and
- Specific files requested by the C2 server.
Once the malware gathers the desired information, it obfuscates (disguises) and encrypts the data before sending it to the cybercriminal’s C2 servers.
Raccoon
The first versions of this malware were observed in 2019 on cybercriminal forums, where it was offered as Malware-as-a-Service (MaaS). Despite the arrest of its primary developer and the dismantling of its infrastructure, Raccoon returned in 2023 with a new version, available by subscription on underground forums.
This updated version of the malware includes the following features:
- Ability to steal information from more than 60 applications,
- It doesn’t perform anti-forensics analysis,
- An interface that allows subscribers to search for credentials,
- Encrypted communication with the C2 server,
- Extensive support for stealing a wide range of cryptocurrency wallets, and
- Ability to take screenshots and capture the victims’ keystrokes (keylogger function).
Panel showing the credentials obtained by the malware. Source: Socradar.
This infostealer can delete the files downloaded during the infection after completing the tasks ordered by the command-and-control server.
Lumma
This infostealer malware appeared in early 2023 and is known for its powerful ability to protect itself against analysis using advanced obfuscation techniques and anti-forensics measures. Like previous versions, it is marketed on underground forums and various Telegram groups. Its great flexibility and lack of dependencies on the local infected system allow it to effectively avoid detection by security systems, such as antivirus software. The creators’ operate on a subscription-based business model, where users can access the data collected by the malware through regular payments.
Criminals typically spread this malware among their victims through cracked or pirated software, in other words, fraudulent applications that allow users to bypass software licensing restrictions. The malware is hidden inside the cracked software and is installed when the user runs the pirated software. Another attack vector involves social media messages and targeted phishing campaigns (spear phishing).
The data Lumma steals and sends to the malware C2 servers include:
- Cryptocurrency wallets,
- Wallets stored in browser extensions,
- Browser user profiles,
- Session cookies,
- Credentials saved in browsers,
- It can extract two-factor authentication data from browser extensions,
- It captures screenshots, and
- It captures operating system information.
Final Thoughts
While malicious software continuously evolves in response to new protection measures, best practices in the use of information technology remain our best defense against most cyberattacks. The primary attack vector continues to be the human factor, due to lack of training or excess trust in illegitimate sources.
Staying vigilant against social engineering attacks, avoiding the installation of software from dubious sources, and enabling two-factor authentication are essential measures to significantly reduce the risk of falling victim to these attacks.
If you haven’t already, we recommend reading our previous article on infostealers.
Sources
RedLine
https://www.infostealers.com/technique/redline-stealer/
https://cyble.com/blog/a-deep-dive-analysis-of-redline-stealer-malware/
https://cybernews.com/security/mac-os-redline-stealer-malware-fake-blockchain-games
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/redline-stealer-a-novel-approach
Raccoon
https://socradar.io/raccoon-stealer-resurfaces-with-new-enhancements
Indicators of compromise (IoC):
https://www.virustotal.com/gui/collection/malpedia_win_raccoon/iocs
Lumma
https://asec.ahnlab.com/en/50594/
Indicators of compromise (IoC):
https://www.virustotal.com/gui/collection/malpedia_win_lumma/iocs
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.