Traffic Abuse at an IXP: How It Happens and How You Can Protect Yourself
December 16, 2024

Internet exchange points (IXPs) play a key role in the interconnection of autonomous networks, allowing different Internet service providers (ISPs) to exchange traffic efficiently.
Like any critical infrastructure, ISPs are vulnerable to malicious attacks. One such threat is traffic abuse. During LACNIC 42 LACNOG 2024, Douglas Fischer gave a presentation on the strategies IXPs can adopt to protect themselves from abusive traffic.
Internet Exchange Points. IXPs are a physical infrastructure that connects multiple networks, allowing them to exchange traffic directly. This reduces dependence on transit providers, improving performance and reducing operating costs. Think of it as a major intersection where different highways converge to optimize the flow of vehicles or, in this case, data packets.
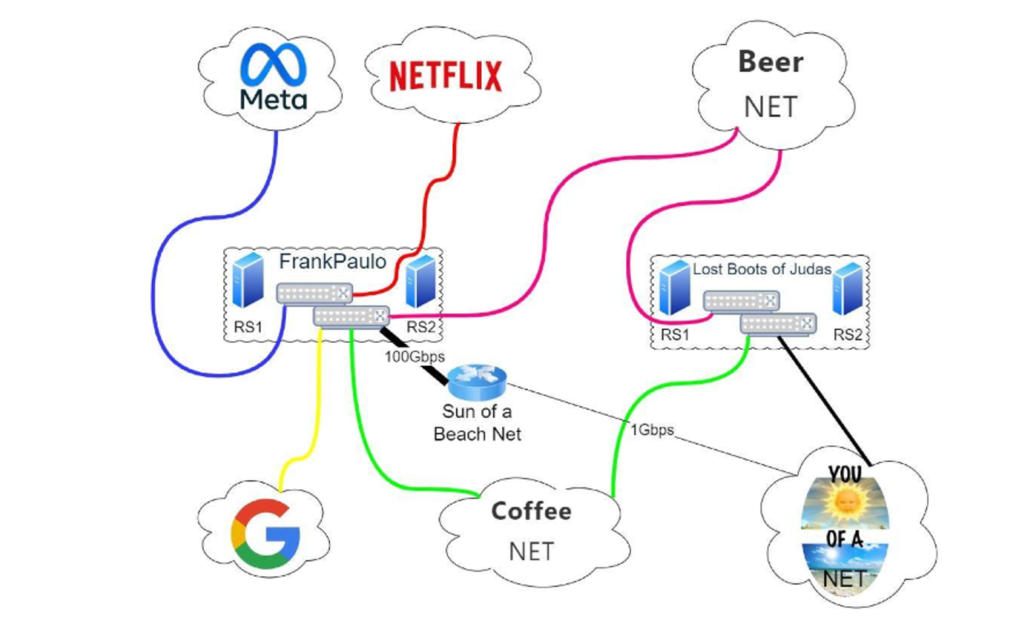
How does the abuse occur? Traffic abuse occurs at an IXP when a network maliciously uses interconnection facilities to transfer traffic to third parties. This can overload the networks that are part of the IXP, generating additional costs and negative impacts on their operations.
Fischer presented some examples, calling one of them a “recipe for mischief”.The‘Sun of a Beach’ network advertises its routes through the servers of an IXP, to member networks such as ‘Juice Net’ and ‘Coffee Net’. These routes are accepted and installed in the member networks’ Forwarding Information Base (FIB).
A Sun of a Beach Net router located in Buenos Aires receives packets destined for Asunción and learns the corresponding routes using iBGP.
This router manipulates the routing policy and changes the packets’ next-hop, redirecting them to the LAN of the IXP belonging to Juice Net and Coffee Net. As a result, traffic is offloaded onto the member networks, thus overloading their resources.
(Free access, no subscription required)
This form of abuse reflects a strategy where traffic is maintained on the network to a point that is further away or until it is delivered incorrectly.
How to protect yourself. According to Fischer, preventing these practices requires monitoring and controlling network traffic. He then explained some basic measures:
- Continuous monitoring: Using tools such as NetFlow, IPFIX or sFlow to collect detailed data about traffic, and analyze this information to identify anomalous patterns that might be a sign of abuse.
- Implementing control policies: His suggestion is to filter unwanted routes on route servers and establish clear policies to accept or reject route advertisements. As for the data, Fischer recommends the use of filtering policies (ACLs) to block malicious traffic. In this sense, he suggests implementing FlowSpec to quickly respond to attacks based on traffic patterns. He also suggests adopting QoS policy propagation through BGP or destination class policies to mitigate the impact of unwanted traffic.
- Transparency and collaboration: In Fischer’s opinion, it is essential to collaborate with other IXP members to define and apply best security practices. It is also important to report malicious behavior to IXP administrators and actively contribute to impact mitigation.
In summary, traffic abuse at IXPs is a challenge that can compromise the stability of member networks and overload valuable resources. A proactive approach, including rigorous monitoring and effective controls, is crucial to preventing such practices.