Thousands of Fortinet Device Credentials Released
21/01/2025

A group of criminals has published on the dark web the config files, IP addresses, and VPN access credentials of more than 15,000 Fortigate devices. Each individual folder contains a Fortigate config dump file and a vpn-passwords.txt file. It was observed that certain passwords were stored as plain text, which may have been due to their lack of complexity or poor system configuration.
It is believed that the leak is associated with a zero-day vulnerability from 2022 (CVE-2022-40684). Hackers exploited this vulnerability by downloading configs from compromised FortiGate devices and adding an administrator account named ‘fortigate-tech-support’. Although these config files were collected in 2022, they reveal a significant amount of sensitive information about network defenses, including firewall rules and credentials.
LACNIC CSIRT analyzed the IP addresses associated with the data breach shared by Kevin Beaumont in his blog.
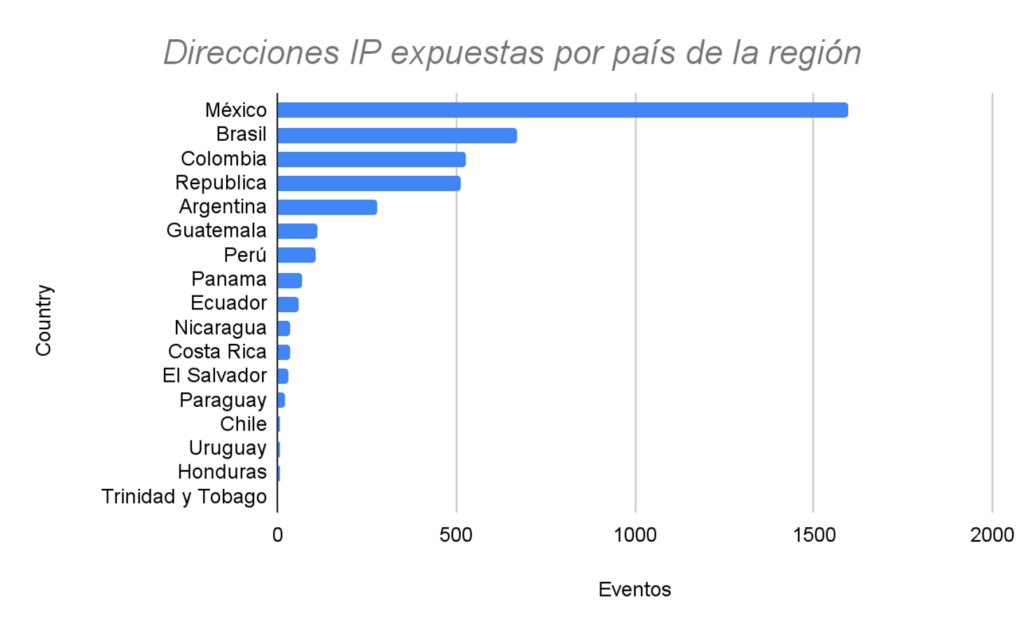
The image above shows the number of IP addresses that were leaked and the countries of the LACNIC region that were affected.
Keep in mind that this already occurred years ago with another vulnerability: https://csirt.lacnic.net/advertencias-de-seguridad/vpn-fortinet-filtracion-de-500-000-credenciales
How to determine if your credentials have been compromised
(Free access, no subscription required)
To find out if your organization’s data is included in the leaked data, we suggest visiting Kevin Beaumont’s blog.
- Update your devices to the latest firmware versions available on the official website
- Disable the HTTP/HTTPS administrative interface or limit the IP addresses from which it can be accessed
- We also recommend following the best practices outlined in the Fortinet documentation
References:
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.