Using DNS for Website Blocking
06/06/2024

By Hugo Salgado, DNS Architect at Tucows Domains
DNS (Domain Name System) blocking is a technique used by network administrators at companies, organizations, and Internet Service Providers (ISPs) to restrict access to certain websites and protect users from inappropriate or malicious content.
In response to suggestions made by participants who completed the course offered by the LACNIC Campus, DNS blocking was included in the LACNIC 41 agenda, where we stressed how it can be implemented to protect users against potentially malicious websites (malware, phishing, etc.), for family and parental controls, and for meeting certain legal requirements.
Network filtering, a common practice on today’s Internet, often uses DNS blocking. DNS blocking can be broad (blocking websites, email, messaging, etc.), a block on an entire domain (URLs cannot be differentiated), or more complex when legitimate services are affected (for instance, if a website is partially hacked, the “legitimate” portion is also blocked).
Our presentation included Response Policy Zone (RPZ), a tool that is very easy to use. This technology is utilized by network administrators to implement DNS response policies. RPZs allow administrators to modify DNS query responses for the purpose of blocking, redirecting, or interrupting access to certain domains. Although it has not yet been formally standardized, this technology is already implemented in well-known open-source DNS systems, and a specification is available on the dnsrpz.info website. The presentation demonstrated an example of its operation and shared instructions for activating RPZ in BIND.
RPZ is a very useful tool that is configured in resolvers. When a client queries a name that matches a pattern, the response is rewritten, preventing the user from reaching a blocked website.
What blocking patterns can be used? Once RPZ is configured, queries to domains or IP addresses can be blocked or redirected based on the policies defined by the carrier or the ISP. Blocks can be implemented based on queried names (exact match or an entire subdomain), name servers (i.e., the server providing the response), an IP address/range in the response, or a client’s IP address.
RPZ can be configured so that end clients receive an error response (“Unable to access the site”) or are redirected to the ISP’s own portal where they are offered more information and warned about the risks of proceeding to the site.
It’s possible to have different “zones” with different RPZ rules, each potentially managed by different units within the organization. Another option is to use external zones maintained by third parties. In other words, different sources are used to implement the blocks.
The image below shows a typical architecture for using RPZ in an organization’s networks.
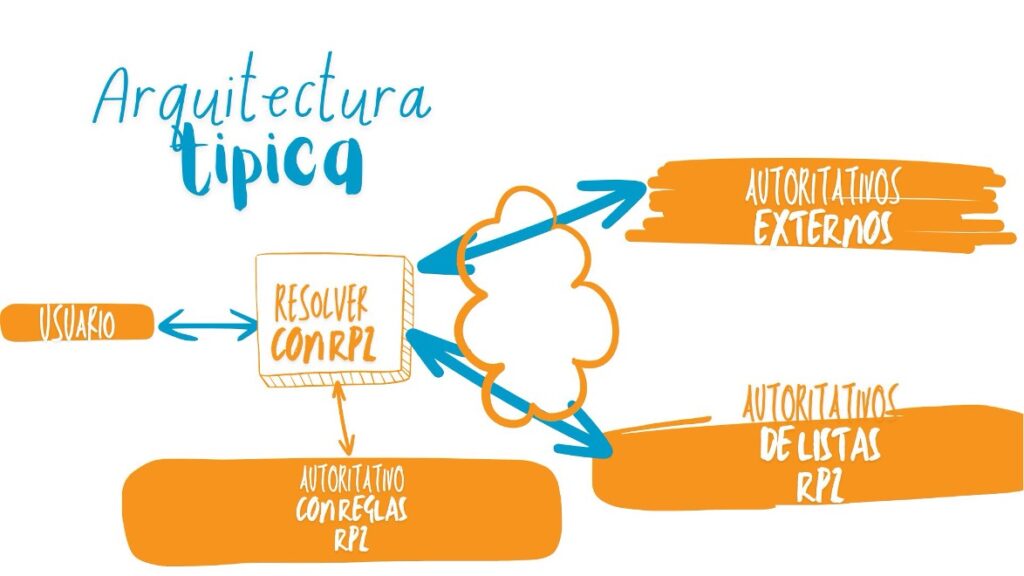
In the future, it would be interesting to standardize the RPZ technique within the IETF, and for national CERTs or CSIRTs to provide lists in RPZ format of sites or addresses that might represent potential threats.
Finally, it should be noted that any block within an organization should be carefully considered and must follow all relevant policies and legislation. DNS blocking should consider issues such as net neutrality, censorship, freedom of expression, and its collateral impact on legitimate sites.
The views expressed are those of the author of this blog post and do not necessarily reflect the views of LACNIC.