How to Manage Blacklisted Resources
16/06/2023

By Guillermo Pereyra – Security Analyst at LACNIC CSIRT
Summary
This topic has been a matter of discussion in different email lists. Also, the LACNIC CSIRT has received reports related to resources from our members that have been included in one or more blacklists. This causes certain issues within their systems, such as the inability to send e-mails or access certain destinations. Therefore, it is clear that there is a growing concern within our community.
This article will address a number of issues associated with Internet resource blacklisting, as well as the causes of blacklisting and the possible steps that may be taken to be removed from such lists.
Introduction
A blacklist is a service provided by an organization to a specific audience. This service periodically publishes a file containing Internet resources that were associated with a security event in the past.These resources may be IP addresses, autonomous system numbers (ASNs) or domain names.
While some organizations offer the service free of charge, others may charge for it. Fundraising can be achieved through two methods: charging service users for access to the file containing the listed resources or requesting payment from the affected organizations to retrieve the listed resources.
To create the list of Internet resources, these organizations rely on systems that detect some type of unusual activity on IP addresses or on reports generated by a community.
Some of the systems used to identify attacks may include honeypots, SSH logs shared by communities, or applications such as fail2ban that can report to a central system.
Disclaimer
LACNIC is not associated with any of the organizations mentioned herein.
This article mentions organizations for informational purposes with the aim of assisting our members in making decisions in case they find themselves in a similar situation.
Possible reasons for being blacklisted
There are various types of blacklists, but generally, the organizations that manage these lists employ distributed honeypot[1] sensors to detect different types of attacks.
Other blacklists are generated from reports made by the community to a central server. When a member of the community detects an IP address that engaged in suspicious activity, it is reported to the centralizer, and the IP address is added to the corresponding blacklist by the organization responsible for the service. Generally, what comes in is included.
IP addresses may be listed for engaging in any of the following categories of activities:
- Brute force attacks: IP addresses that have attempted to gain unauthorized access to real systems or honeypot sensors.
- Denial-of-service attacks: IP addresses that have been involved in carrying out a denial-of-service attack. These IP addresses could belong to systems infected with malware, such as Mirai, or they could be systems that have a vulnerable protocol being exploited for carrying out these attacks. Further information on this topic can be found in our related projects.
- Spam or marketing campaigns: IP addresses that sent unsolicited emails.
- Suspicious content: IP addresses used to store or distribute malware, host phishing websites, or malicious sites.
- Services exposed to the Internet or misconfigured servers: IP addresses from the TOR network, Open Relay SMTP, Open Proxy, missing PTR records, etc.
Issues associated with blacklists
The main concern is not being included in these blacklists, but rather the use administrators make of them to block these resources.
If an administrator uses a blacklist that collects IP addresses that have been sending spam, they will typically block these IP addresses to prevent receiving emails from those sources.
On the other hand, if the blacklist is associated with infrastructure attacks, such as failed SSH access attempts, the administrator will block the corresponding resource from establishing connections to the infrastructure they manage.
There are blacklists with different levels of granularity. For example, the administrator may proceed to block the entire IP prefix to which the IP address belongs. In extreme cases, they may even list all the prefixes associated with an Autonomous System Number (ASN).
How to verify if a resource is blacklisted
In order to verify the listed resources, it is necessary to go through each organization that manages these lists individually.
Usually, these organizations provide either a downloadable file, DNS queries, dashboard with data, or a service with an API that can be queried.
To go through these blacklists, you can develop your own system or use solutions that are already available. Within the existing resources, there are online platforms that provide free analysis through blacklists, as well as open-source code available in public repositories. However, it is important to note that some of the open-source solutions may lack regular maintenance or updates.
The following are two online analysis tools, but there are others as well: MXToolbox and DNSChecker.
Steps to take when a resource is blacklisted
Taking into account that each blacklist has different objectives, the first step we must take is to verify the type of blacklist on which the resources are listed. This will help determine the appropriate course of action to address the situation effectively.
- Perform an analysis to determine whether the listed IP corresponds to a client with a static or dynamic IP, or if it is an address that is used internally by the organization.
- When an IP resource is listed on a spam-related blacklist, it can lead to various situations and require different solutions, including:
- Vulnerable mail servers: If the system was compromised, it is necessary to reinstall the system completely to make sure that there are no backdoors left behind.
- Misconfigured servers: Our mail server may be configured to allow mail relay[2] from any host on the Internet. Another possible reason is that the DNS server does not align the A or AAAA record for our mail server with the PTR record for its corresponding IP address (FCrDNS[3]).
- Compromised email accounts: If a user’s access to their mail server is compromised by falling for phishing or malware and an attacker is using this box to send spam.
- Vulnerable operating systems: In most cases, compromised resources are personal computers that have been infected with malware. However, it is important to note that IoT devices can also be susceptible to compromise. In such scenarios, it is crucial to identify the compromised device and take necessary measures to remove the malware. Another measure is to manage the use of port 25 for clients that are domestic or should not typically send mail. For more information on this topic, please refer to the suggested reading section.
- Analyze and determine if the resource is listed due to a compromised system within the network. In such cases, it is essential to identify the affected system and carry out the necessary procedures to eliminate the malware.
- If the IP resource is hosting malware or phishing, it is necessary to remove the malicious website or resource. In certain cases, this task involves contacting the client to request collaboration in resolving the issue.
- It is sometimes difficult to find the affected system as some blacklists may not provide evidence such as logs, domains, URLs or timestamps. In such situations, it is necessary to rely on other platforms specialized in detecting attacks or misconfigured systems exposed to the Internet.
Certainly, as a solution to the problem, it is important to consider notifying the network administrator that we are unable to access. It is important to reach out to the relevant party to request the removal of the block on our resources or to be added into a whitelist. We can make use of the whois point of contact, a response center that has contact with the administrators, community mailing lists, website contact. In the event that email communication is inaccessible from our network, we should look for alternatives such as social networks, use of reliable proxies, or phone calls, among other options.
Resource sites
There are numerous online services that provide information and analysis for this purpose, many of which are based on honeynet communities or conduct scans to generate reports displayed on their websites.
MiLACNIC Security Module
The technical and administrative users of MiLACNIC can access the security reports found in the system’s security module.
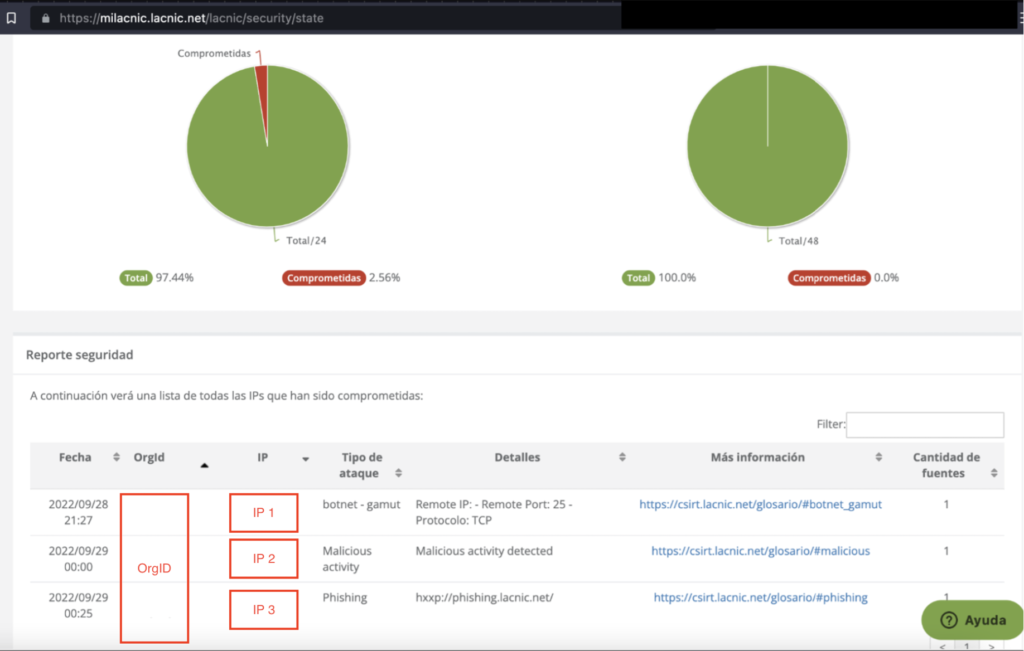
Image 1. MiLACNIC Security Module Dashboard
The IP addresses involved in any of the mentioned activities are shared with the respective organization to which they have been assigned through the MiLACNIC Security Module Dashboard.
This data is collected through our distributed sensor network, which includes our members’ networks and trusted organizations that provide us with this information. For more information on this project, please refer to the recommended readings at the end of the article.
IBM XForce
An exchange platform for sharing engagement indicators. It is possible to enter an IP or IP prefix, or some other indicator of engagement in the search engine.
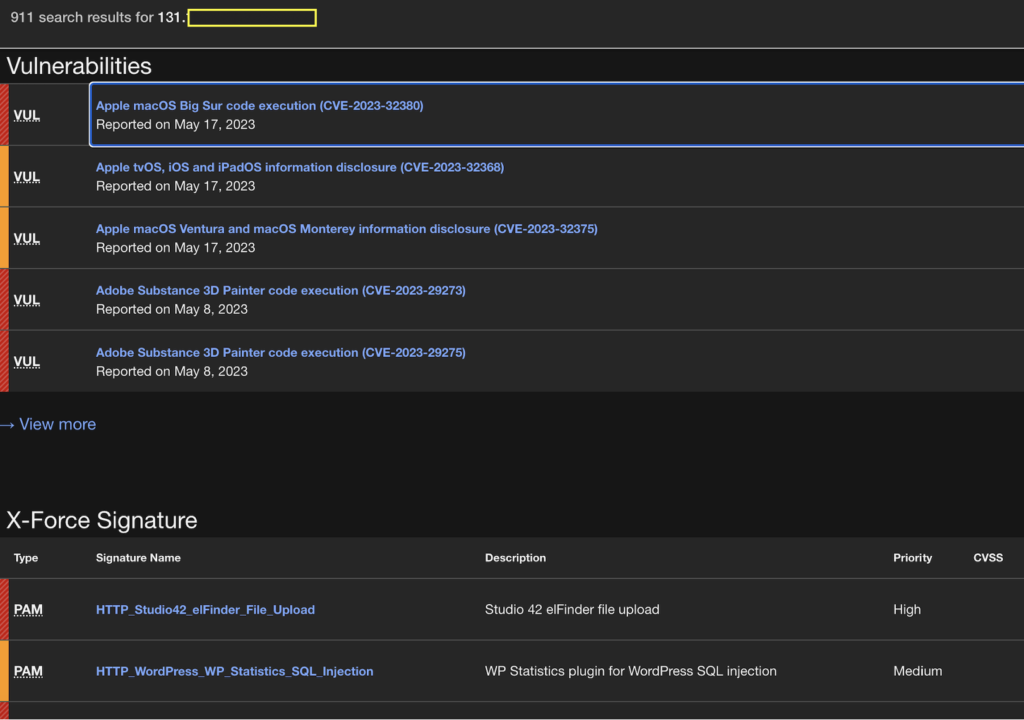
Image 2. Example of using IBM XForce to find IP-related issues.
Web: https://exchange.xforce.ibmcloud.com/
Open Threat Exchange (OTX)
This platform has the same functionalities as the previous one. Both platforms allow entering the listed IP address to obtain information about threats associated with that specific address.
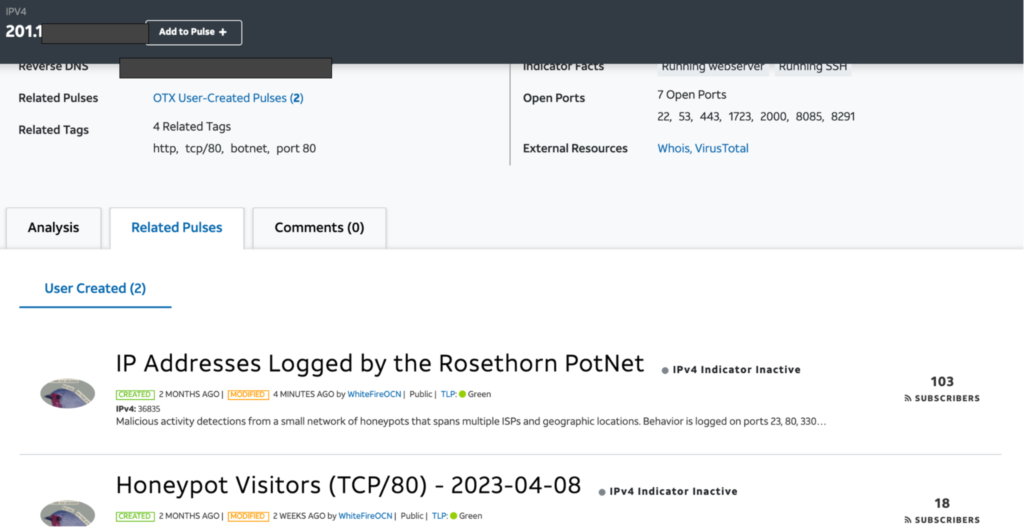
Image 2. Example of using OTX to find IP-related issues.
Web: https://otx.alienvault.com/
Other available platforms
The following platforms perform scans of IP resources and offer free information regarding exposed services that could potentially be exploited by attackers, leading to the listing of the IP resource.
Shodan – https://www.shodan.io/
Censys –https://censys.io/
Shadowserver – https://shadowserver.org/
There are other similar platforms that could be used.
Final thoughts
It is important to be well-informed about how blacklists operate and understand the necessary actions to be taken if resources managed by the organization are listed.
It is necessary to understand the possible causes of blacklisting and to take specific actions to address the issue. By taking these measures, we can prevent blockages and restrictions on user or customer access to Internet services.
It is worth noting that each blacklist operates with its own specific procedure for removing a resource from the Internet that has been listed on the blacklist. Some a may require a fee for the removal of a resource, while others offer temporary removal with the possibility of re-listing if the issue recurs. In a following article, we will go through some blacklists to provide a more detailed explanation of this aspect.
Suggested reading material
Port 25 Management by NiCbr/CGIbr/CERTbr
https://www.antispam.br/estatisticas/
https://www.cgi.br/media/docs/publicacoes/1/CadernoCGI_Estudos1_Ingles.pdf
[1]Software that simulates a vulnerable system to detect attacks.
[2] https://es.wikipedia.org/wiki/Open_relay
[3] https://es.wikipedia.org/wiki/Forward_confirmed_reverse_DNS