Short Message Service : Security Alternative or Obsolete Technology?
21/11/2024

By César Díaz, Head of Telecommunications Affairs at LACNIC
In an increasingly digital world, security is no longer an option, but an essential responsibility. From our personal data to corporate and government information, the need to safeguard credentials and prevent unauthorized access is vital. In this landscape, a technology once considered obsolete, Short Message Service (SMS), has re-emerged as a basic component in digital security. Far from being just a messaging tool, SMS has established itself as an alternative for implementing two-factor authentication (2FA). Yet its use as a security measure inevitably raises the question: Is SMS truly reliable for 2FA?
From basic messaging to essential security
In its early days, SMS revolutionized mobile communications, allowing users to exchange text messages quickly and easily. During the 1990s and early 2000s, it dominated the communications landscape. However, with the advent of instant messaging and social media apps, SMS began to lose its prominence. What few anticipated was that, far from falling into oblivion, this technology would become an ally in digital security.
Today, SMS is no longer merely a tool for personal communication — it has become a resource for authenticating and validating sensitive information. Companies and governments around the world have adopted SMS as a reliable channel that adds an extra layer of security to their platforms. From e-commerce to access credentials, SMS is now widely used to deliver verification codes, providing an additional barrier against cyberattacks. This function has positioned them as a critical resource in the fight against fraud and cyber threats.
Why does SMS remain relevant to security?
Despite the development of more advanced technologies, there are several reasons why SMS remains an important tool in security:
- Universal compatibility: SMS works on virtually all mobile phones, regardless of brand, operating system or age of the device. This makes it an accessible and universal option, as it caters to both users of the latest smartphones and those with more basic devices.
- Ease of use: Unlike other authentication technologies, SMS does not require users to install additional applications or complex configurations. Anyone with a mobile phone can receive and use SMS to verify their identity, and this contributes to its widespread adoption, even in areas with low levels of digitalization.
- Reliability in low-connectivity areas: SMS does not rely on the Internet, meaning it can operate in areas with limited or unstable connectivity. This makes it a particularly useful option in rural areas or during emergency situations.
- Global accessibility: SMS knows no borders. SMS messages can be sent and received anywhere in the world, provided that there is interoperability between mobile messaging service providers, a topic we will expand on later.
The role of SMS in 2FA
2FA is one of the most effective security mechanisms available today, and SMS plays a key role in this ecosystem. In SMS-based 2FA, users must complete two layers of verification before gaining access to an account or service. The first layer is typically a password, while the second is a temporary code or one-time password (OTP) sent via SMS to the user’s phone.
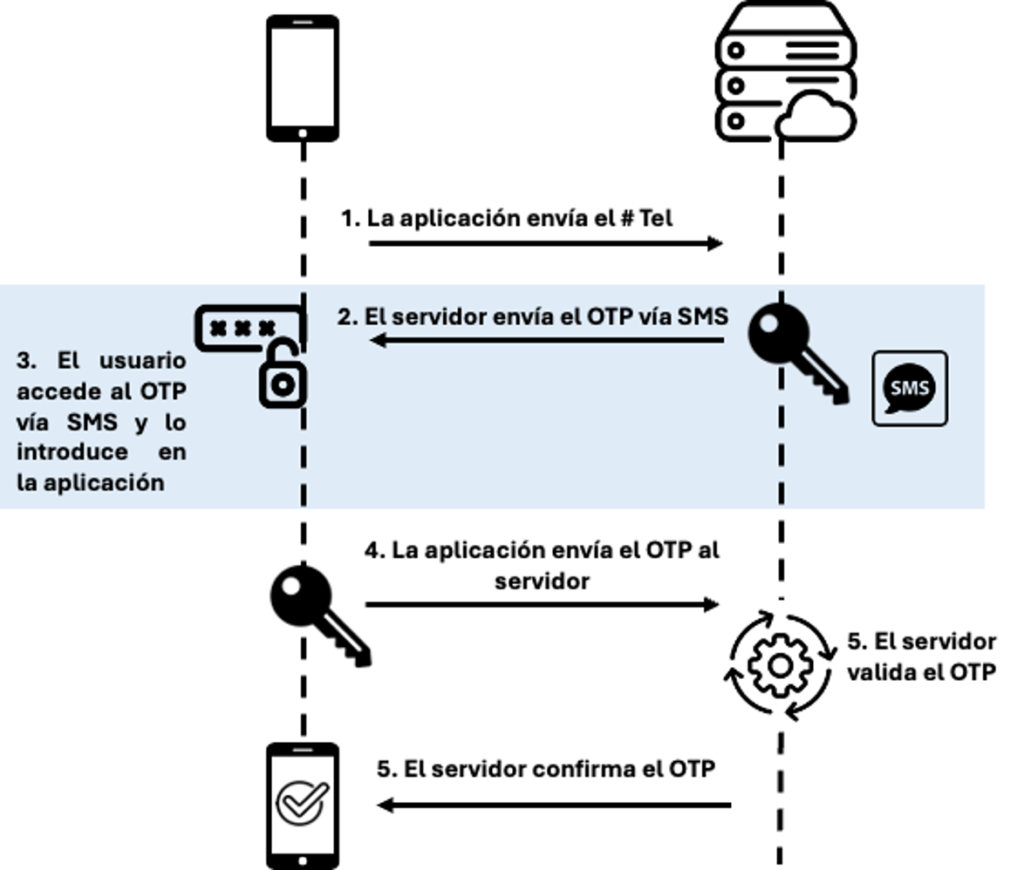
This dual-layer verification drastically reduces the likelihood of an attacker accessing sensitive information, even if they manage to steal the user’s password. By relying on two different factors (something the user knows and something they possess) SMS adds an extra layer of protection against hacking, phishing, or unauthorized access attempts.
(Free access, no subscription required)
Do SMS have 2FA vulnerabilities?
While SMS-based two-factor authentication (2FA) is effective, it comes with significant risks and vulnerabilities that we should not ignore. A clear example is SIM swapping, as demonstrated by the 2019 attack on Jack Dorsey, co-founder of Twitter. Attackers managed to transfer his phone number to a SIM card under their control, allowing them to access his personal account. This incident shows just how devastating this type of attack can be, as a simple SIM change can compromise the security of sensitive accounts.
Another major risk is SMS interception on insecure networks. In 2017 and 2018, vulnerabilities were discovered in Signaling System No. 7 (SS7), a protocol used by mobile networks to exchange information between operators. This decades-old protocol is essential for managing SMS authentication, routing, and transmission. In one notorious case in the United Kingdom in 2019, cybercriminals managed to intercept verification codes sent by banks to their customers, which allowed them to gain access to bank accounts and fraudulently transfer money.
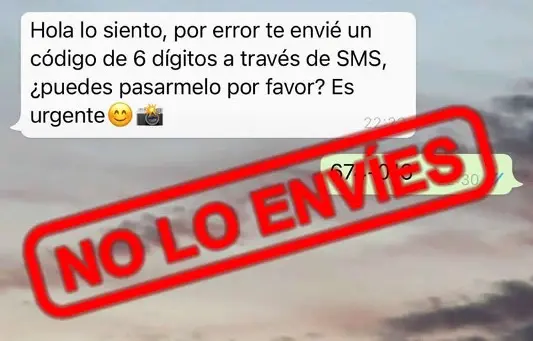
Lastly, social engineering techniques are a significant threat to SMS-based 2F. A common example involves WhatsApp, where cybercriminals attempt to access the victim’s account by sending a login request. In response to this request, WhatsApp sends a verification code to the user’s number via SMS. The attacker, posing as a friend or contact, then sends a message to the victim saying something like this:
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.