A Year of Increasingly Sophisticated Security Incidents
04/01/2024

By Graciela Martínez, Head of LACNIC CSIRT, and Guillermo Pereyra, Security Analyst at LACNIC
Last year, security incidents in the region have become increasingly advanced and sophisticated, exploiting new methods to deceive individuals and organizations. These conclusions can be derived from the reports generated by LACNIC CSIRT to understand the state of the Internet resources under our administration.
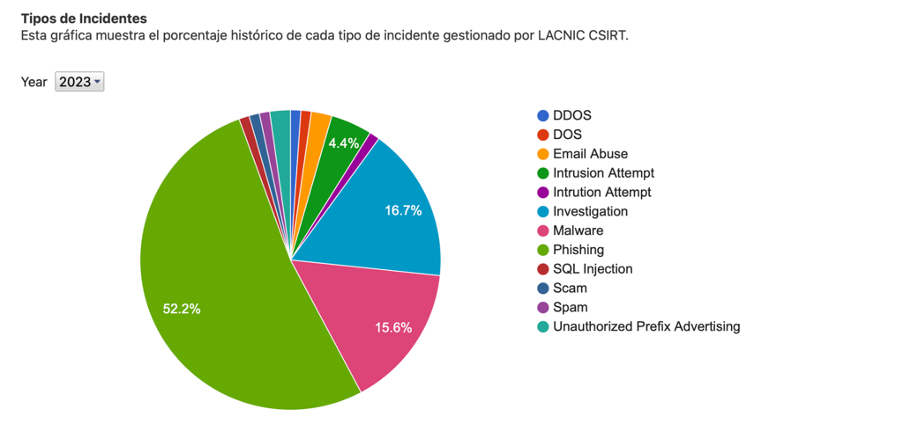
Phishing and spam for malicious purposes, whether originating from or directed towards resources in the region, continue to be the most frequently reported incidents at our CSIRT.
Data collected from collaborating organizations and our own sources indicate a clear evolution of statistics towards these phishing and spam episodes.
Why are attacks becoming more sophisticated? Attackers now gather intelligence and don’t always go directly for the organization. Their goal is often to exploit the supply chain and they attempt to attack an organization from the periphery, through a supplier, or a client.
For instance, when an attacker successfully breaches a client (who typically has fewer defenses), they obtain valid credentials and use them to access your email accounts. Once the attacker has gained access to a legitimate account, they attempt to deceive the staff of the organization that is the ultimate target of the attack. In this regard, they have advanced toward a more sophisticated form of identity theft, as the malicious link is part of a legitimate email, which makes it more difficult to detect.
Our primary recommendation is to reinforce the policies related to safeguarding information security, considering the risks to which it is exposed, and actively working on raising awareness among employees.
(Free access, no subscription required)
Malware. Reports from third parties regarding malware in their networks have also increased significantly in the region. Botnets are employed as malicious agents to attack the victim.
Last year has also seen an increase in ransomware attacks on smaller organizations. This trend is closely associated with the goal of cybercrime, namely, economic gain.
Cybercriminals now operate within organized structures akin to traditional criminal structures. As cybercrime evolved, it transitioned from attacking individuals to targeting organizations and, more recently, entire networks.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.