The Risks of Ignoring IPv6 in Your Network
23/10/2024
By Carolina Badano, Communications Coordinator at LACNIC
During his presentation at the LACNIC 42 LACNOG 2024 event held in Asunción Paraguay, Henri Alves de Godoy, network analyst and professor at Campinas University, stressed the urgent need to monitor dual-stack networks and underscored the risks of ignoring the IPv6 protocol. The key aspects of his presentation are highlighted below.
IPv6. What is the current state of connectivity?
Despite living in an era where most devices support IPv6 and where adoption rates have already exceeded 50% in countries such as Mexico, Brazil, and Uruguay, Alves noted that it is common for people to approach him saying that they don’t have IPv6 in their networks. “This is a misconception and, at times, a risk because these people don’t understand why the provider does not make use of the global address,” he added.
Moreover, cybercriminals and botnets continue to evolve and are using IPv6.
According to Alves, many honeypots (sensors that collect information about threat actor behavior on the Internet) are not yet configured to collect data over IPv6, and some threat intelligence reports continue to ignore the protocol. The image below shows the percentage of malicious behavior not identified by any security layer.
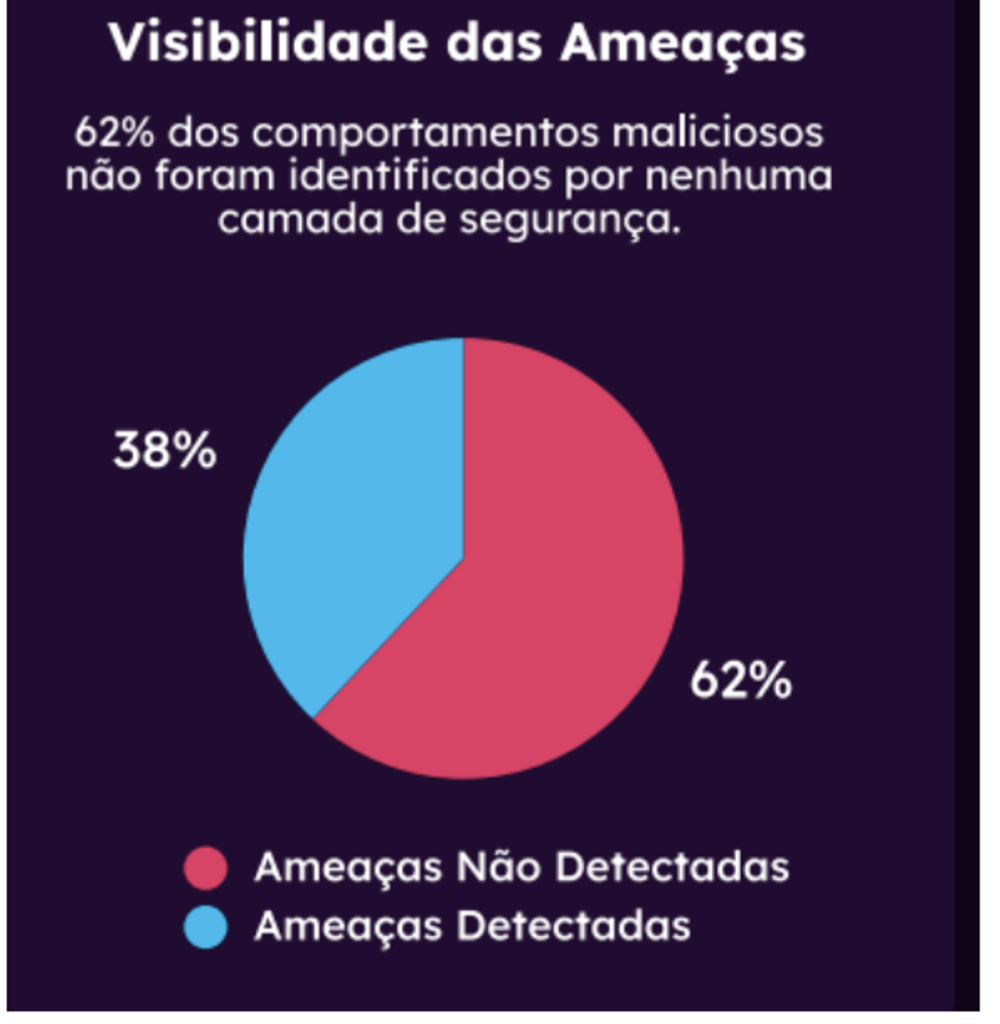
Source: Morphus Cyber Threat Resilience Report, 2022
As a result, Alves concluded that a portion of traffic is currently not being analyzed, adding that this issue should not be ignored and must be addressed urgently.
What are the risks of ignoring IPv6 in our networks?
When operators ignore the presence of IPv6 in their networks, they cannot implement robust access controls or traffic filters. A simple scan of the IPv4 network could reveal the existence of an IPv6 address, which would allow hackers to move laterally within the internal systems and thus escape detection mechanisms.
Alves presented three practical examples (tested in a controlled lab environment) that can occur if we don’t monitor IPv6 traffic:
- Automatic tunnels: compromise user experience and divert traffic
In some operating systems, these methods are automatically enabled and, if not properly monitored, can redirect traffic, exposing critical vulnerabilities. Tunnels can also create openings for data exfiltration, if employing IPv6 packets encapsulated in IPv4 in a communication that is not properly monitored and protected.
- Data exfiltration in unmonitored networks: uses secret channels and can be used for intentional secret data transfers. It is difficult to detect because it uses legitimate protocols and ports (for more information, see the following article on infostealers).
Exfiltration via ICMPv6:
The ICMPv6 protocol is essential for IPv6 operation and is mainly used for network diagnostic purposes, for example, sending “ping” packets. However, cybercriminals can abuse this protocol to exfiltrate data, using ICMPv6 packets to transport sensitive information.
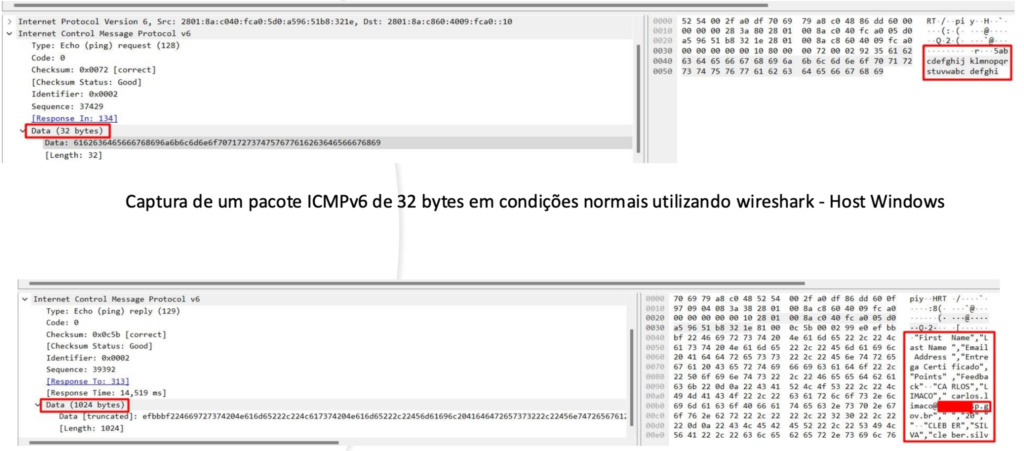
Figure 1
In Figure 1, an attacker can use ICMPv6 to encapsulate data contained in a confidential spreadsheet into 1024-byte packets that are invisible to monitoring solutions, as these tend to focus on higher layers, such as the application layer.
Exfiltration via Flow Label
Because it is considered harmless, the Flow Label field in the IPv6 header is a feature often ignored by security systems. However, it can be used to create secret communication channels, storing and transmitting data without the traffic being identified as suspicious.
In Figure 2, with a tool such as IPv6teal, an attacker can hide data, for example system password files (passwd in the case of Linux), inside the Flow Label field. Because Flow Label is a legitimate field, it goes unnoticed by intrusion detection systems (IDS) or firewalls that are not configured to monitor it.
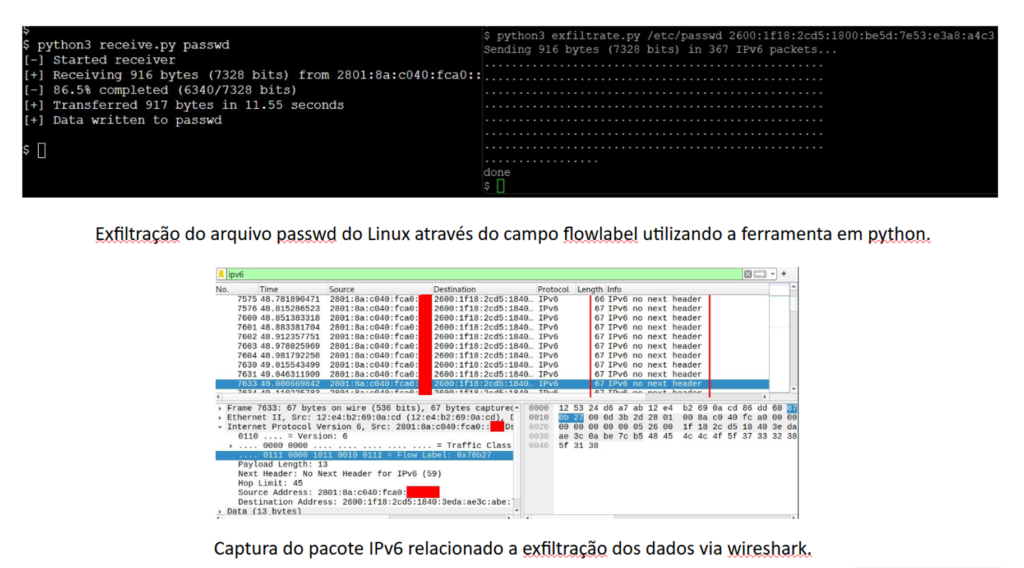
Figure 2
- Unauthorized Router Advertisements (RA). Since all devices can receive an IPv6 address, an unauthorized advertisement can modify network behavior, potentially leading to violations of security policies.
Alves recommends analyzing the actual need to keep router advertisements in datacenters and servers.
The main issues are:
- Connectivity disruptions: An unauthorized RA might cause devices to automatically switch to IPv6, bypassing the security policies configured for IPv4. This can lead to connectivity failures or expose the network to new types of attacks.
- Security policy vulnerabilities: Networks often have robust policies in place for IPv4, but an automatic transition to IPv6 can create significant openings, as firewall rules and other control mechanisms may not be configured for IPv6 traffic.
For instance, an unauthorized RA could cause a server to switch from IPv4 to IPv6, bypassing the firewall rules configured for IPv4. This would allow malicious traffic to be routed with no restrictions, exposing the network to attacks. Implementing tools such as RA Guard can help mitigate this type of threat, but it is crucial that security policies are aligned for both IPv4 and IPv6.
During the LACNIC41 meeting, Ernesto Sanchez presented his work titled IPv6 Security Analysis with Containerlab, which deals precisely with the application of RA Guard. This presentation is available at https://lacnic41.lacnic.net/es/programa/presentaciones-y-videos
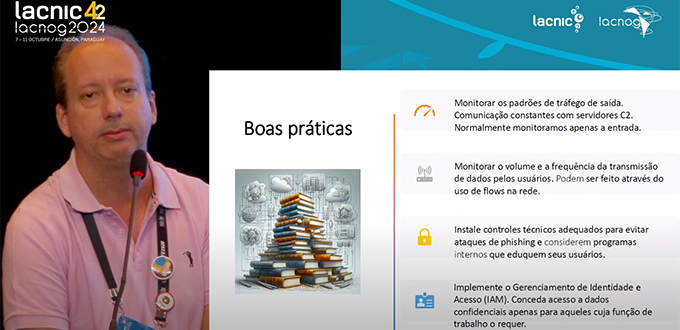
To conclude, Alves provided a series of best practices that should be considered:
- Monitor outbound traffic patterns
- Monitor the volume and frequency of data transmission by users (this can be done by analyzing network flows)
- Install proper technical controls to avoid phishing attacks
- Implement identity and access management (IAM)
In conclusion, IPv6 integration and monitoring are essential, and IPv6 should never be disabled. “This is a crime that people commit,” Alvez stressed.
Furthermore, we must adequately prepare our teams to manage dual-stack networks effectively.
Currently, security information and event management (SIEM) systems have some limitations when used in dual-stack environments. Therefore, it is necessary to develop strategies for an effective integration for both the IPv4 and the IPv6 protocols in security systems.
Click here to watch Henri Alves’s presentation.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.