A Persistent Threat: Critical Vulnerability in Network Devices
25/04/2024

By Guillermo Pereyra, Security Analyst at LACNIC CSIRT
A known vulnerability
In mid-October 2023, CISCO published CVE-2023-20198, a vulnerability that affects the user interface (web UI feature) of Cisco IOS XE software.
This vulnerability allows gaining unauthorized access to an exposed web interface and execute commands for creating a user.
In this article, we will discuss how this vulnerability affects the Latin American and Caribbean region, what measures LACNIC CSIRT is taking, and what we can do to fix this problem.
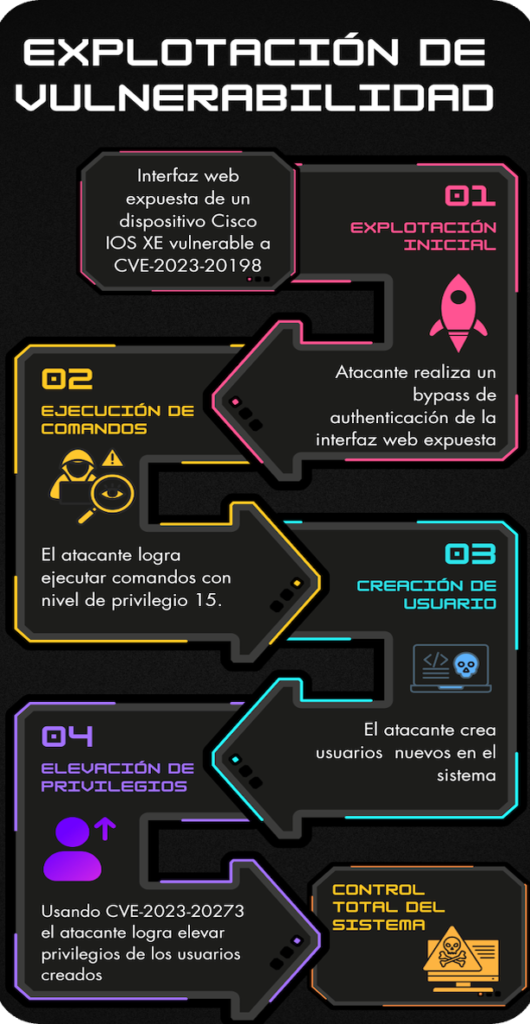
A vulnerability that affects our region
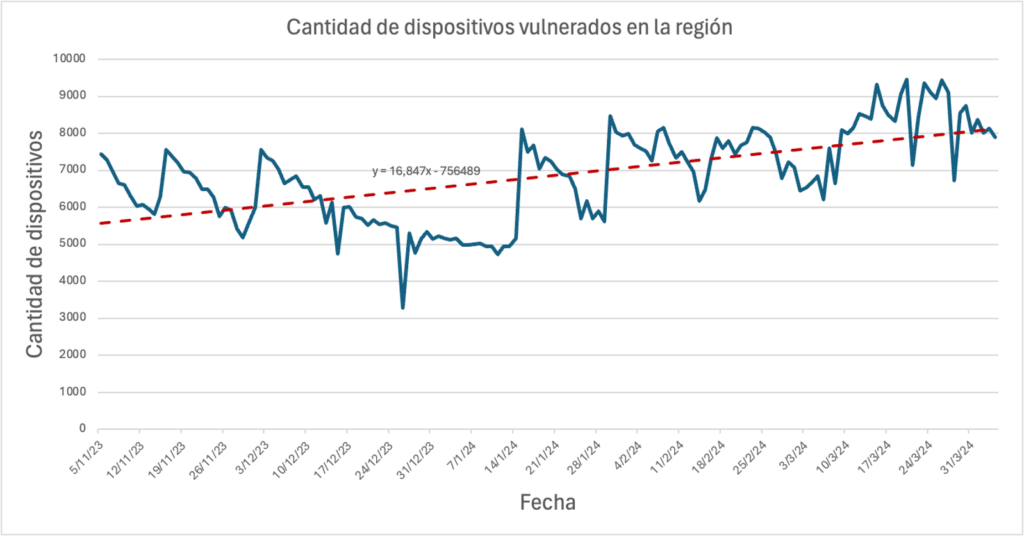
At LACNIC CSIRT, we’ve noticed an increase in the number of devices in the region affected by this vulnerability since its publication.
Data shows that an average of 17 compromised devices have been detected daily over the last five months, as illustrated in the graph below.
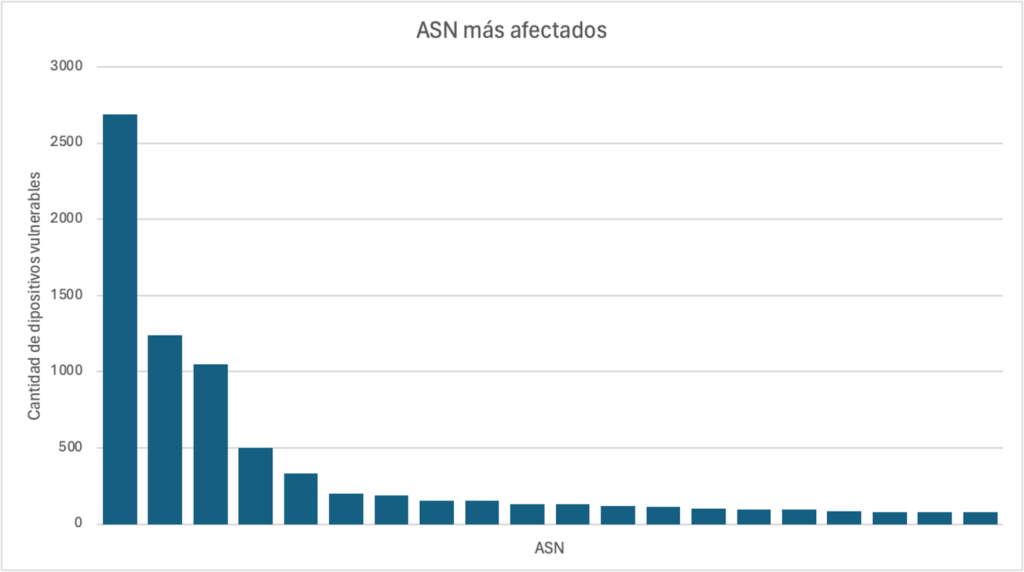
An analysis of the data shows that the problem affects approximately 900 different ASNs. In the following graph, it is interesting to see how the problem is concentrated in just a few ASNs.
Although updates and fixes have been available for over five months, thousands of network devices are still vulnerable to this problem.
Actions taken by LACNIC CSIRT
The LACNIC response team informs organizations with an exposed IOS XE web service that they might be vulnerable.
We alert them through the MiLACNIC security module so that the organization can identify and mitigate any possible threat that may be occurring on their networks.
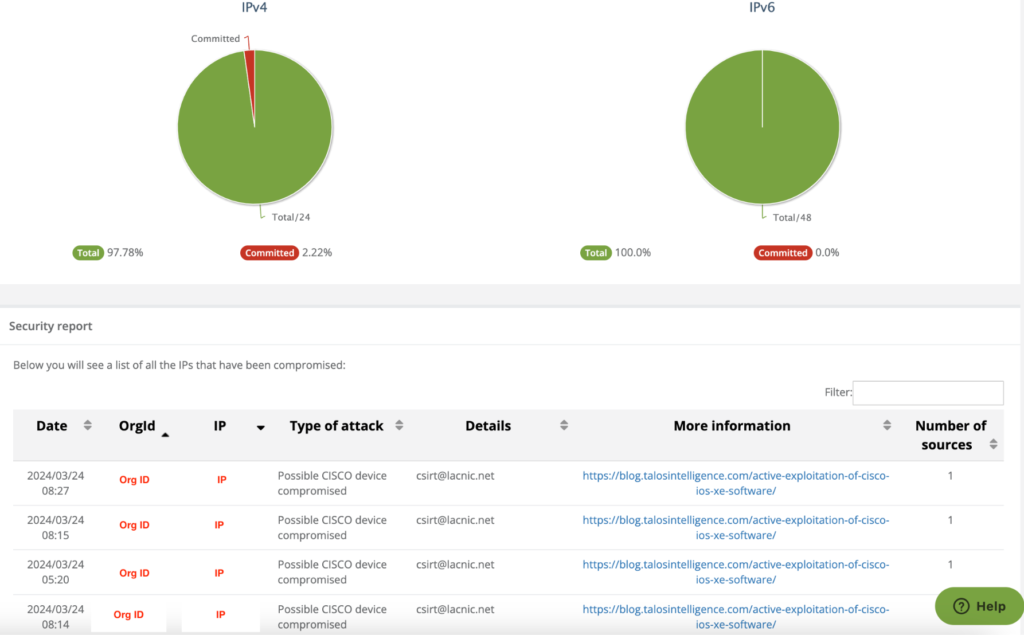
Detecting and fixing the vulnerability
How do I know if my device is vulnerable?
A device is vulnerable if the web interface of the following IOS XE versions is exposed:
| CPE configuration | Affected version (from) | Affected version (up to and including) |
|---|---|---|
| cpe:2.3:o:cisco:ios_xe:*:*:*:*: *:*:*:* | 16.12 | 16.12.10a |
| cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:* | 17.3 | 17.3.8a |
| cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:* | 17.6 | 17.6.6a |
| cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:* | 17.9 | 17.9.4a |
Has my device been attacked?
The verifications recommended by TALOS, CISCO’s security team, include:
- Check the system logs for the presence of any message that includes the “user” field associated with an unknown user.
%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line
%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023
- Check the system logs for any unknown files in the “filename” field:
%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename
How can I fix this?
To fix the problem, the recommendation is to update the devices. Temporarily disabling web management until the proper update has been installed or reducing exposure by blocking access to the Internet can be used as mitigating measures. For more information on how to mitigate this risk, we recommend visiting the CISCO website (included under References).
Summary
The number of devices affected by the CVE-2023-20198 and CVE-2023-20273 vulnerabilities is on the rise in Latin America and the Caribbean. Although these vulnerabilities were identified and fixed five months ago, many devices remain vulnerable. Several proofs of concept and exploits have been published for these vulnerabilities. This leads to an increase in attacks by malicious actors.
At LACNIC CSIRT, we have been actively working to address this problem by using tools such as MiLACNIC to alert organizations to the risks and help detect and mitigate potential threats on their networks. It is important for organizations to take steps to protect their devices, including updating their software or implementing the recommended mitigation measures.
We also request that you disseminate this article among organizations that may be using these devices.
RECOMMENDATION
Organizations are urged to immediately install any applicable updates.
References:
https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
https://csirt.lacnic.net/articulos-y-novedades/modulo-de-seguridad-de-milacnic
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of LACNIC.